Howard Solomon, recognized leader in IT reporting, just published an article on my RESCAT theory, as well as other issues related to cybercrime and social engineering.
What is social engineering
Social engineering is an attempt to convince someone to act in a predetermined manner that may or may not be in their best interest of doing so. Social engineering begins at the earliest stages of our lives; when we attempt to convince our parents to provide us something we want, or to act in a particular way, and vice-versa. As we develop, we quickly learn, being consciously aware or not, that we have the ability of trying to achieve what we want by appealing to others human nature, human curiosity, and a series of emotions.
The six emotions commonly targeted through social engineering
Fear, greed, guilt, helpfulness, obedience, and urgency. Cybercriminals regularly design their phishing attacks based on social engineering, and target one or more of these emotions to cause us to react in specific ways:
Fear:
Threats to personal or organizational well-being. We “fear” that if we do not do as instructed to information contained in an email for example, that we may suffer some form of consequence.
Greed:
An attempt to obtain something for oneself that provides significant rewards.
Guilt:
Non-cooperation results in significant retribution.
Helpfulness:
Our propensity to be helpful to others requesting our assistance or support.
Obedience:
Response to a person of authority.
Urgency:
The fear of missing out if we do not respond quickly such as notifications or offers pertaining to expired subscriptions, credit cards, or free offers. Also, cybercriminals use urgency as an emotion when orchestrating CEO scams that involve urgent messages that appear to originate from a CEO or other executive instructing others to process payments to others in an expeditious manner.
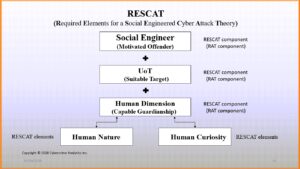
When confronted by a social engineered cyberattack, we can process a number of different paths of decision-making prior to making our final decision that will determine whether we become victimized by a social engineered cyber attack:
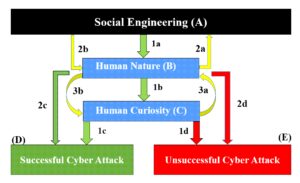
My research continues to expand on RESCAT as I work with other scholars to advance new ways to educate users of technology (UoT) how to become more aware of when they are exposed to someone attempting to manipulate their actions when engaged with technology and facing a cyberattack – particularly those that incorporate various forms of social engineering.
You can read Howard Solomon’s article published October 29, 2020 here.
